Top Qs
Timeline
Chat
Perspective
Serpent (cipher)
Block cipher From Wikipedia, the free encyclopedia
Remove ads
Serpent is a symmetric key block cipher that was a finalist in the Advanced Encryption Standard (AES) contest, in which it ranked second to Rijndael.[2] Serpent was designed by Ross Anderson, Eli Biham, and Lars Knudsen.[3]
Like other AES submissions, Serpent has a block size of 128 bits and supports a key size of 128, 192, or 256 bits.[4] The cipher is a 32-round substitution–permutation network operating on a block of four 32-bit words. Each round applies one of eight 4-bit to 4-bit S-boxes 32 times in parallel. Serpent was designed so that all operations can be executed in parallel, using 32 bit slices. This maximizes parallelism but also allows use of the extensive cryptanalysis work performed on DES.
Serpent took a conservative approach to security, opting for a large security margin: the designers deemed 16 rounds to be sufficient against known types of attack but specified 32 rounds as insurance against future discoveries in cryptanalysis.[5] The official NIST report on AES competition classified Serpent as having a high security margin like MARS and Twofish and in contrast to the adequate security margin of RC6 and Rijndael (currently AES).[2] In final voting, Serpent had the fewest negative votes among the finalists but ranked in second place overall because Rijndael had substantially more positive votes, the deciding factor being that Rijndael allowed for a far more efficient software implementation.[citation needed]
The Serpent cipher algorithm is in the public domain and has not been patented.[6] The reference code is public domain software, and the optimized code is licensed under the GPL.[7] There are no restrictions or encumbrances regarding its use. As a result, anyone is free to incorporate Serpent in their software (or in hardware implementations) without paying license fees.
Remove ads
Key schedule
Summarize
Perspective
The Serpent key schedule consists of 3 main stages. In the first stage the key is initialized by adding padding if necessary. This is done in order to make short keys map to long keys of 256-bits, one "1" bit is appended to the end of the short key followed by "0" bits until the short key is mapped to a long key length.[4]
In the next phase, the "prekeys" are derived using the previously initialized key. 32-bit key parts XORed, the FRAC which is the fraction of the Golden ratio and the round index is XORed with the key parts, the result of the XOR operation is rotated to left by 11. The FRAC and round index were added to achieve an even distribution of the keys bits during the rounds.[4]
Finally the "subkeys" are derived from the previously generated "prekeys". This results in a total of 33 128-bit "subkeys".[4]
At the end the round key or "subkey" are placed in the "initial permutation IP" to place the key bits in the correct column.[4]
Key schedule in C++
#define FRAC 0x9e3779b9 // fractional part of the golden ratio
#define ROTL(A, n) ((A) << n | (A) >> 32-n)
uint32_t key[8]; // key provided by user
uint32_t subkey[33][4]; // roundkeys
const uint8_t S[8][16] = {}; // S-boxes
/* key schedule: get prekeys */
void get_pre(uint32_t w[4*33], const uint32_t k[8]) {
uint32_t x[4*33+8];
for (int i = 0; i < 8; i++)
x[i] = k[i];
for (int i = 8; i < 140; i++) {
x[i] = ROTL(x[i-8] ^ x[i-5] ^ x[i-3] ^ x[i-1] ^ FRAC ^ (i-8), 11);
w[i-8] = x[i];
}
}
/* key schedule: get subkeys */
void get_sk(const uint32_t w[4*33], uint32_t (*sk)[4]) {
uint8_t i, p, j, s, k;
for (i = 0; i < 33; i++) {
p = 32 + 3 - i;
for (j = 0; j < 4; j++)
sk[i][j] = 0;
for (k = 0; k < 32; k++) {
s = S[p % 8][((w[4 * i + 0] >> k) & 0x1) << 0 |
((w[4 * i + 1] >> k) & 0x1) << 1 |
((w[4 * i + 2] >> k) & 0x1) << 2 |
((w[4 * i + 3] >> k) & 0x1) << 3 ];
for (j = 0; j < 4; j++) {
sk[i][j] |= ((s >> j) & 0x1) << k;
}
}
}
}
void key_schedule() {
uint32_t w[4*33];
get_pre(w, key);
get_sk(w, subkey);
}
S-boxes
The Serpent s-boxes are 4-bit permutations, and subject to the following properties:
- a 1-bit input difference will never lead to a 1-bit output difference, a differential characteristic has a probability of 1:4 or less.[8]
- linear characteristics have a probability between 1:2 and 1:4, linear relationship between input and output bits has a probability between 1:2 and 1:8.[8]
- the nonlinear order of the output bits as function of the input bits is 3. However there have been output bits found which in function of the input bits have an order of only 2.[8]
The Serpent s-boxes have been constructed based on the 32 rows of the DES s-boxes. These were transformed by swapping entries, resulting arrays with desired properties were stored as the Serpent s-boxes. This process was repeated until a total of 8 s-boxes were found. The following key was used in this process: "sboxesforserpent".[4]
Remove ads
Permutations and transformations
Initial permutation (IP)
The initial permutation works on 128 bits at a time moving bits around.
for i in 0 .. 127
swap( bit(i), bit((32 * i) % 127) )
Final permutation (FP)
The final permutation works on 128 bits at a time moving bits around.
for i in 0 .. 127
swap( bit(i), bit((4 * i) % 127) )
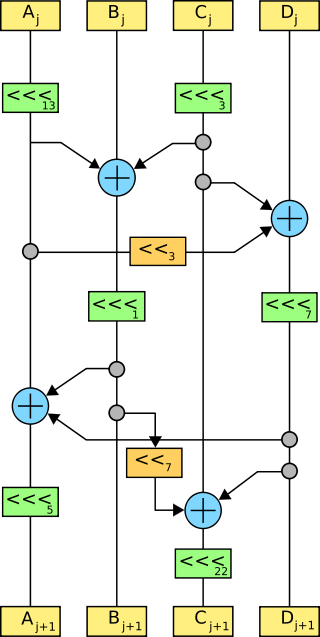
Linear transformation (LT)
Consists of XOR, bit shift left and bit rotate left operations. These operations are performed on 4 32-bit words.
// The input is the result of key mixing and substitution.
for (short i = 0; i < 4; i++) {
X[i] = S[i][B[i] ^ K[i]];
}
// Linear transformation.
X[0] = ROTL(X[0], 13);
X[2] = ROTL(X[2], 3 );
X[1] = X[1] ^ X[0] ^ X[2];
X[3] = X[3] ^ X[2] ^ (X[0] << 3);
X[1] = ROTL(X[1], 1 );
X[3] = ROTL(X[3], 7 );
X[0] = X[0] ^ X[1] ^ X[3];
X[2] = X[2] ^ X[3] ^ (X[1] << 7);
X[0] = ROTL(X[0], 5 );
X[2] = ROTL(X[2], 22);
// The output becomes the new state.
for (short i = 0; i < 4; i++) {
B[i + 1] = X[i];
}
Rijndael vs. Serpent
Rijndael is a substitution-linear transformation network with ten, twelve, or fourteen rounds, depending on the key size, and with key sizes of 128 bits, 192 bits, or 256 bits, independently specified. Serpent is a substitution–permutation network which has thirty-two rounds, plus an initial and a final permutation to simplify an optimized implementation. The round function in Rijndael consists of three parts: a nonlinear layer, a linear mixing layer, and a key-mixing XOR layer. The round function in Serpent consists of key-mixing XOR, thirty-two parallel applications of the same 4×4 S-box, and a linear transformation, except in the last round, wherein another key-mixing XOR replaces the linear transformation. The nonlinear layer in Rijndael uses an 8×8 S-box whereas Serpent uses eight different 4×4 S-boxes. The 32 rounds mean that Serpent has a higher security margin than Rijndael; however, Rijndael with 10 rounds is faster and easier to implement for small blocks.[9] Hence, Rijndael was selected as the winner in the AES competition.
Remove ads
Serpent-0 vs. Serpent-1
The original Serpent, Serpent-0, was presented at the 5th workshop on Fast Software Encryption, but a somewhat tweaked version, Serpent-1, was submitted to the AES competition. The AES submission paper discusses the changes, which include key-scheduling differences.
Security
Summarize
Perspective
The XSL attack, if effective, would weaken Serpent (though not as much as it would weaken Rijndael, which became AES). However, many cryptanalysts believe that once implementation considerations are taken into account the XSL attack would be more expensive than a brute force attack.[citation needed]
In 2000, a paper by Kohno et al. presents a meet-in-the-middle attack against 6 of 32 rounds of Serpent and an amplified boomerang attack against 9 of 32 rounds in Serpent.[10]
A 2001 attack by Eli Biham, Orr Dunkelman and Nathan Keller presents a linear cryptanalysis attack that breaks 10 of 32 rounds of Serpent-128 with 2118 known plaintexts and 289 time, and 11 rounds of Serpent-192/256 with 2118 known plaintexts and 2187 time.[11]
A 2009 paper has noticed that the nonlinear order of Serpent S-boxes were not 3 as was claimed by the designers. Specifically, four elements had order 2.[8]
A 2011 attack by Hongjun Wu, Huaxiong Wang and Phuong Ha Nguyen, also using linear cryptanalysis, breaks 11 rounds of Serpent-128 with 2116 known plaintexts, 2107.5 time and 2104 memory.[1]
The same paper also describes two attacks which break 12 rounds of Serpent-256. The first requires 2118 known plaintexts, 2228.8 time and 2228 memory. The other attack requires 2116 known plaintexts and 2121 memory but also requires 2237.5 time.
Remove ads
See also
- Tiger – hash function by the same authors
Footnotes
Further reading
External links
Wikiwand - on
Seamless Wikipedia browsing. On steroids.
Remove ads